Stop Building Higher Walls: Why 2026 Is the Year of Resilience
How to shift the priority away from prevention
As we look toward 2026, the paradigm governing enterprise security is undergoing a critical, overdue transformation. For years, the dominant philosophy has been rooted in absolute breach prevention—the Sisyphean task of building walls high enough to stop every single threat.
However, a recent Dark Reading forecast highlights a brutal reality: in the age of AI-driven velocity, that model is officially broken. For founders scaling from Seed to Series C and beyond, the question is no longer “How do we stop everything?” but rather, “How fast can we recover when an attack succeeds?“.
The Myth of Absolute Prevention
The current state of security is defined by two unsustainable trends:
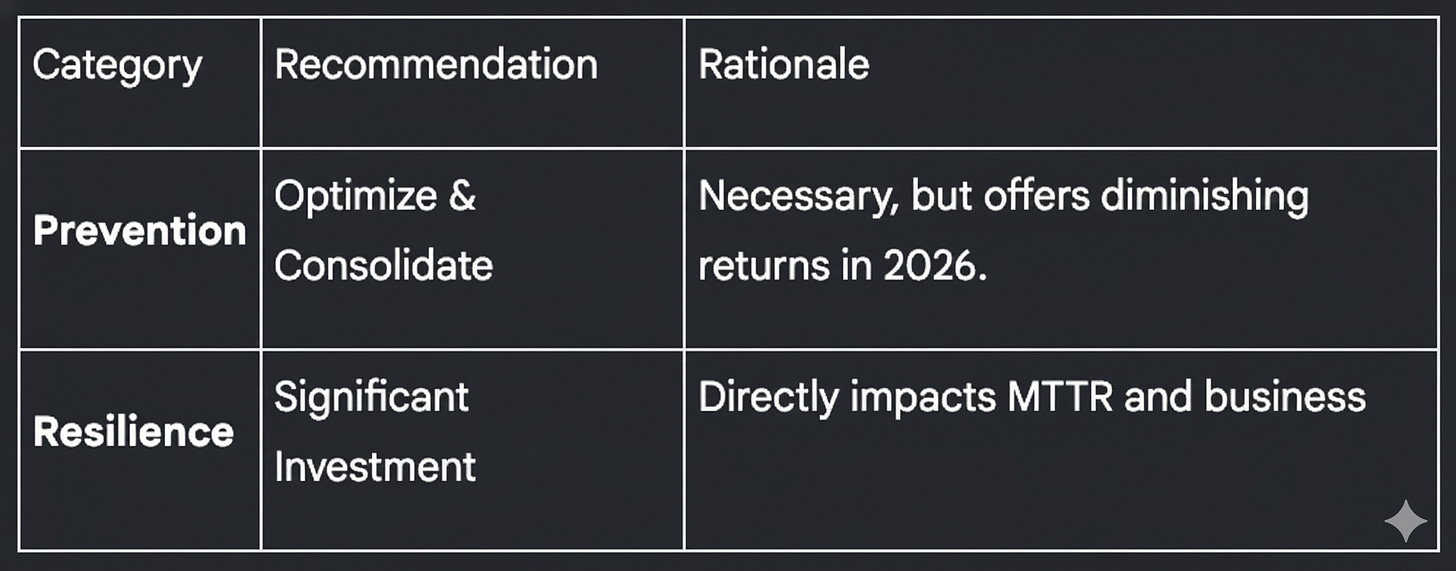
1. Unmanageable Tool Sprawl: The average enterprise now wrestles with 76 distinct security tools. Most of this spend is dedicated to perimeter defense, which often leads to alert fatigue and slower response times.
2. AI-Driven Velocity: AI-driven threats—like polymorphic malware and deepfake social engineering—now outpace our ability to manually triage alerts. The window between initial compromise and lateral movement has shrunk from days to mere hours .
In short, we are playing a game of digital whack-a-mole where the moles are faster than the humans holding the mallets.
The Only Metric Your Board Actually Cares About
In the boardroom, traditional reports on “attacks blocked” are losing relevance. If you want to protect your company from regulatory scrutiny and shareholder litigation, you need to focus on one metric: Mean Time to Recovery (MTTR).
The difference between a “4-hour recovery” and a “4-day recovery” isn’t just a technical detail—it’s the difference between a manageable incident and a market-shaking crisis that destroys shareholder value.
Think of it like modern building codes: instead of trying to build a 100% fireproof house (prevention), we install high-end sprinkler systems and fire-resistant materials to ensure that if a fire starts, the structure doesn’t collapse and we can move back in quickly (resilience).
The 30% Resilience Audit
As you plan your next budget cycle, I recommend a quick audit of your security spend. If you are a founder or CTO, ask your team: What percentage of our budget goes to resilience vs. prevention?
The Rule of Thumb: If your spending on resilience capabilities—like automated backups, disaster recovery, and identity security—is under 30% of your total budget, you are budgeting for 2016, not 2026.
Practical Steps for Growing Startups
You don’t need more tools; you need better ones. Here is how smart CTOs are navigating this shift:
• Assume Breach: Shift your mindset. Stop asking “if” and start planning for “when”.
• Consolidate Vendor Bloat: Move away from niche, single-purpose tools. Look for integrated platforms (like XDR) that prioritize detection and recovery workflows.
• Prioritize the Core: Invest in immutable backups and automated incident response playbooks. These are the tools that actually “bounce back” the business.
• Clearer Accountability: Fewer tools mean fewer dashboards and a clearer line of sight for incident ownership.
Final Thoughts
The future of security success isn’t about being unhackable; it’s about being unbreakable. By shifting your focus from “higher walls” to “faster recovery,” you protect not just your data, but your company’s long-term viability.
I’d love to hear from you: Have you audited your resilience spend lately? Drop a note below or reach out if you’re looking for a template for your next board deck.
Thanks, and see you all again next week!